From an objective point of view, the amount of trust that people put with companies based on the Internet is pretty astounding. In addition to providing whatever product or service they offer, these companies are often given highly sensitive information with hardly a second thought from the consumer. Here, we’ll review how millions of people learn that this trust was misplaced each year, why these companies want all this data in the first place, and how important it is to follow a few data collection best practices in your own business.
ImageSys LLC Blog
The smartwatch has quite a few benefits, but anything that one might bring to the table is offset drastically by its position as a threat magnet. Vulnerabilities in smart watches and other wearable technology makes using these devices somewhat risky behavior. Today, we will look at some of the features of the modern smartwatch, how hackers are utilizing them to be disruptive, and what you need to do to protect yourself from the risk posed by hackers.
Data security isn’t the easiest thing in the world to plan for, especially if your organization doesn’t have any dedicated security professionals on-hand. While protecting your data with traditional methods, like passwords, firewalls, and antivirus, is important, what measures are you taking to make sure a thief or hacker isn’t just walking into your office and making off with your technology?
The modern office can be a pretty monotonous place. When people do similar tasks over and over again, their attention to detail can wane. That may be a problem for your operational efficiency, but depending on what the expectations are, it likely won’t end your company. Ransomware, on the other hand, can be a major problem for any organization it affects. Today, we will share with you how to get your staff to care about the looming threats that target businesses from over the Internet.
I think by now most people understand just how dangerous ransomware is. Even with some of the ridiculous names they have like Gandcrab, Jigsaw, and WannaCry. Hell, two strains even have names from the James Bond canon: LeChiffre and GoldenEye. But one funny-named strain of ransomware, SamSam, has been devastating information systems for sometime, and has caught the eye of several U.S. law enforcement agencies.
Mobile devices are great tools that allow for enhanced mobility and convenience, but this increased accessibility is also a major detriment in terms of data security. Mobile devices are notorious for being considerable security threats to businesses that utilize them. Therefore, businesses that use mobile devices on a regular basis should absolutely be aware of how they can influence security policies.
As technology advances and improves at an exponential rate, it is little wonder that today’s youth are growing up with a closer relationship to technology than any other generation before them. While this has opened up many beneficial opportunities for them, it can also be the source of many serious issues without the proper supervision.
Uh oh. It’s the big day, and you’ve just realized that you’ve forgotten to purchase a gift for a special someone (or twelve). Thank goodness for online shopping, right? However, you still need to keep your digital security in mind as you try to save the holiday--cybercriminals aren’t the type to take a break during one of the most potentially lucrative times of year.
How often have you started to read something you thought may be valuable to you, only to put it down a few moments later, completely lost because of the use of technical language and industry jargon? The IT industry can be especially guilty of this. However, since this is need-to-know information, we’ve decided to go over a few crucial security concepts by representing your business security with a locked door.
In the realm of cyberattacks, a data breach is perceived as one of, if not the biggest threat that a business can face. They are seen as so dangerous, in fact, that threats like phishing attacks are largely disregarded. However, data from a recent study suggests that this is the opposite of what should happen in a decision maker’s mind.
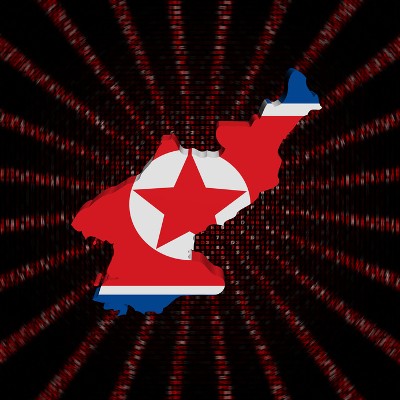
According to the homeland security adviser to the White House, Tom Bossert, international blame for the global WannaCry attack is being directed toward North Korea. Responsibility for the attack that spanned from May 12th to the 15th of 2017 has been firmly placed on the Democratic People’s Republic of Korea, which Bossert says is in agreement with the conclusions of Australia, Canada, Japan and New Zealand.
No technology lasts forever. Your business will need to replace server hardware or workstations eventually, no matter how well you take care of it. However, what do you do with the hard drive of any device that you have to replace? If you don’t take action to destroy your old hard drive (after moving any data off of it as needed), you could be in violation of various compliance guidelines issued by HIPAA.
It is our hope that you are aware of how much of a risk spyware can pose to your business. Your business generates, collects, and leverages truly considerable amounts of data each day that is intended for your business only. While spyware that is introduced by a hacker is clearly a bad thing, what if the manufacturer of the device installed a program that pulled data from your machine?
In recent years, how-to guides and YouTube videos have brought renewed enthusiasm for the phrase ‘Do It Yourself’. From services that will ship all the ingredients needed for a home-cooked meal right to your front door to a kit that contains all of the building materials one needs to make a fully functioning ‘tiny house’, DIY kits have made it easier for someone who is less than an expert to successfully complete a project or learn a skill. The Dark Web has taken this infatuation with ‘DIY’ to a whole new level with a rising increase in the sale of Ransomware kits.
When considering your business’ security, it is only too easy to overlook how information of any kind might be compromised. Take, for example, the case study that is provided by the fitness application Strava, the jogging app that shares more data than many, including the United States military, would prefer.
It’s no secret that a business relies on its data. Therefore, it only becomes more important that this data is protected, especially in light of the predictions that have been made for the rest of the year concerning ransomware. Read on for a closer examination of these predictions, and suggested actions that you can take to protect your business and its data.
Passwords are everywhere. It seems that every account requires a password, in addition to the devices we use to access these accounts. This is a good thing, as it only helps to increase security - assuming that the password is strong. After all, a password that anyone can guess can hardly be called a password at all.
Email is a solution that needs to be protected, lest you expose important information to any onlookers while messages are in transit. Encryption is one of the key ways you can make sure that your messages are safe, but email hasn’t always used this method to secure messages. In fact, it wasn’t until relatively recently that encryption became a staple of the major email providers.